Phishing is still a Huge Security Issue

Phishing is still a Huge Security Issue

It amazes me how many people still fall victim to phishing schemes. Even with a mail filtering security service in place; I still get these daily. It doesn’t matter where my email account is hosted, Google, Microsoft, etc. We have to start teaching our friends/family/employees what to look for, what to do when they are unsure, and what to do when they receive these kinds of email. So lets talk about the two basic ways hackers use email to phish for user information and malicious access.
1. Phishing Email with Links to Hacker Controlled Websites
These are emails that are sent from bogus email addresses and made to look like an automated service or notification of a problem that requires you to respond. It typically links to an infected website, the owner/operator usually as no idea they have been hacked and this content exists. The webpage you land on looks exactly like a Microsoft, Google, UPS, Bank or other provider’s page; however, the address in the browser address bar is a dead give away that you are not where you think you are. It may already be to late if you have opened the linked page. New file-less scripts embedded in infected websites can execute PowerShell commands in the background on unprotected Microsoft Windows platforms that will connect back to a server and download a virus payload in the background without you being aware. Within minutes a malicious program is executed and a hacker has access to your system to do what he wants.
The second thing they get you to do is enter your email address and password information into a fake login screen that captures it and returns an error. Your first instinct is that you entered the wrong password, so you enter it again or possibly a different one. Most users use this information to access social media and financial accounts with commons passwords. You have now given a hacker what he needs to access you email, social media accounts, possibly your financial information, and much more. If you visit one of these pages by accident, unplug your computer from the network, run a virus scan and use a program like Malwarebytes to detect and remove any threats. I would also change your passwords to sites that use what you entered ASAP only after your machine is cleaned.
2. Phishing Emails that contain Attachments
This is a huge issue for many still. Because people fall victim to the scam I described above, hackers will email infected attachments to your contacts with your return address. These d not usually show up in your “Sent” folders because hackers use scripts to mass email these infected PDF, RTF, and Office documents. Since they are from a known contact, they open these attachments and infect their computer as well. I shared an article on one of the biggest crimes committed by a hacking group targeting the hospitality and catering industry. some of these hackers were recently brought to justice and their methods exposed. I would definitely read this article to get an understanding of how this is happening. You can find the detailed article here. If you open one of these attachments by accident, unplug your computer from the network, run a virus scan and use a program like Malwarebytes to detect and remove any threats. I would also change your passwords to sites that use what you entered ASAP only after your machine is cleaned.
How can I tell if it is a Phishing email?
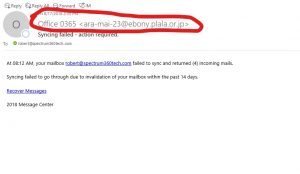
The easiest way to look at the detailed email address in the email header which shows where it was sent from. For example:
Office O365 <pola-shou@a02.itscom.net>
or
Office Mail <no-reply-update-##CHAR##.upda-te-q53bpel7@reycon.com>
Obviously neither of these is from Microsoft but many mail programs only show you the first part outside of the actual email address. This is know as the short or friendly name that is for display purposes only and has no real unique information.
Secondly, does the email make sense? Does it contain ncorrect grammar or language? Getting an invoice from someone you don’t usually do business with? It is very important to use common sense when getting questionable email.
What to do if your not sure
When you receive anything questionable, forward it to your IT department, IT Services Provider, or Email provider to check. All of these mentioned will either know if it is legitimate or have a way to test the attachment in a safe “Sandbox” environment for malicious content. They will then advise you how to proceed.
Also be aware that it is very important to report these to you IT people so they can take preventative steps to advise employees and block sources that send these malicious emails. It is not enough to avoid it. Share what you found so others can avoid the same pitfalls. If you encounter an infected website, inform the owner so they can clean the website and block hackers from getting the information. We need to be proactive to start making a dent in cyber crime.
Solutions that can Protect you and your Business
If you have read any of my blogs, I always talk about solutions. Fully Managed Cloud-based Solution like Quasar Cloud can secure your business from threats like these even when someone falls into these kinds of pitfalls. We can minimize the damage, prevent data loss and provide enterprise level managed security all businesses need today to mitigate these threats. Simply click here to set an appointment so we can discuss what you need.
I believe in strength through education, and I work for a living like the rest of you. Thank you for sharing my thoughts on this topic and please drop me a line if you have any questions. I would like to help you with your business.
D. Robert Trembath
VP of Technology Services
rtrembath@quasardata.com